Golden Rules for Modern Microservice Development
🌐 From 12-Factor to Cloud Native: Golden Rules for Modern Microservice Development
In the era of cloud-native architecture, Microservices have become a core pattern in software engineering. But Microservices are more than just "breaking down a monolith into several services." To truly make a system scalable, maintainable, and highly available, we need to follow a systematic design philosophy.
And this philosophy is the 12-Factor App principles (originally proposed by Heroku) – which remain a foundational methodology for building high-quality Microservices today.
This article combines modern technology ecosystems (such as Kubernetes, Docker, CI/CD, cloud services, etc.) to explain in detail how the 12-Factor App principles can be implemented and evolved in today's Microservice development.
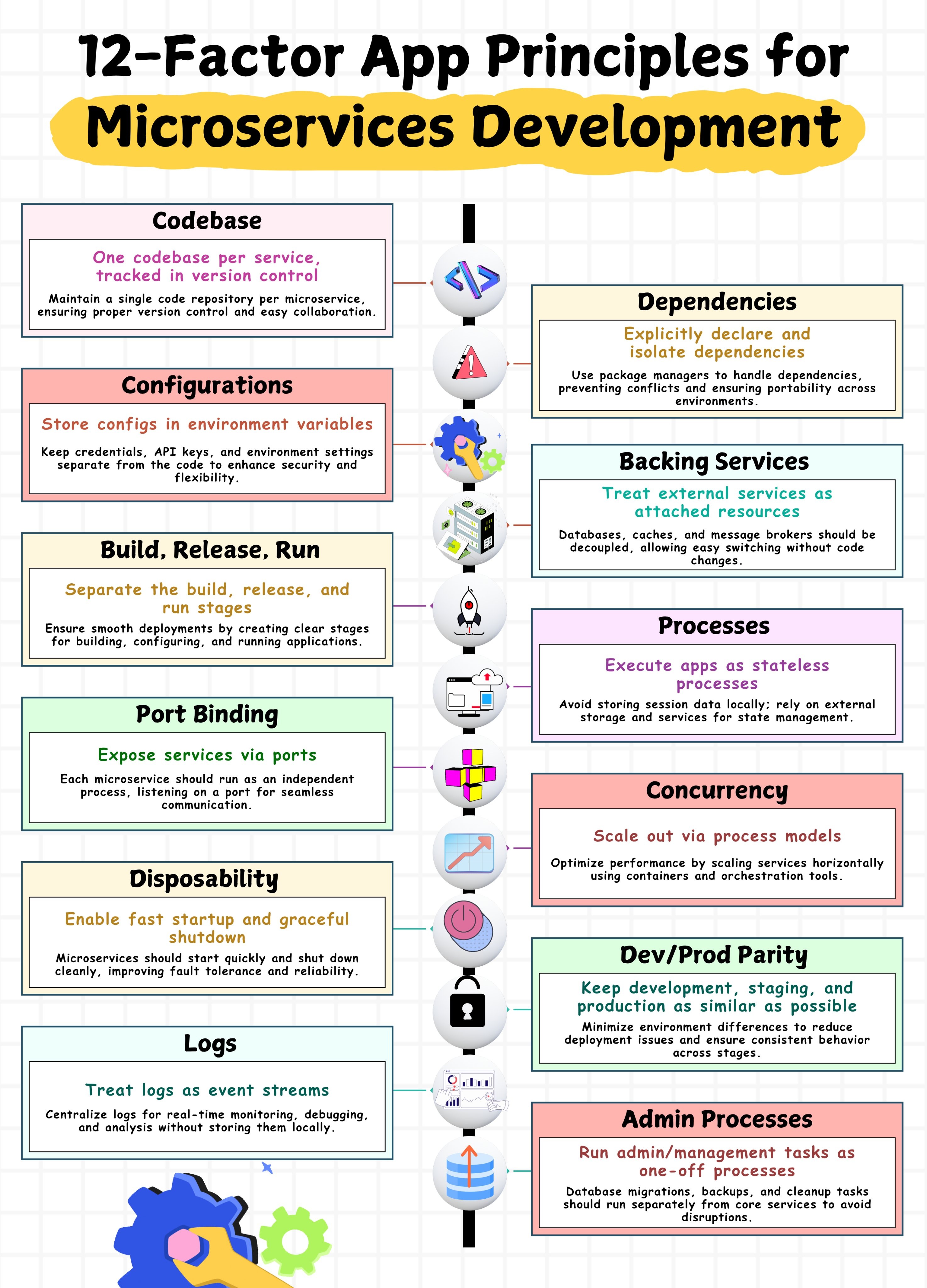
1️⃣ Codebase — Single Codebase, Version Trackable
Principle: Each Microservice maintains only one code repository (Repo) and manages it through a version control system (such as Git).
In modern Microservice architecture, “One Service One Repo” is the most common practice.
This not only ensures independent deployment and permission isolation but also allows services to adopt different technology stacks and lifecycles.
🔧 Modern Extension:
- Use Monorepo + Nx/Turborepo to manage large system dependencies;
- Use GitOps (ArgoCD/Fleet) to combine Git repositories with deployment status.
2️⃣ Dependencies — Explicitly Declare and Isolate Dependencies
Principle: All dependencies must be explicitly declared and isolated from the system environment.
In Microservices, each container or runtime environment should have its own dependency list (such as requirements.txt, package.json, go.mod, etc.) to avoid the problem of "it runs on my machine."
🔧 Modern Practice:
- Use Docker image layer caching + lock files (such as
poetry.lock) to ensure build consistency; - Use package repository proxy (such as Nexus, Artifactory) for unified dependency management.
3️⃣ Configurations — Externalize Environment Configurations
Principle: All configurations (API Key, database connection, etc.) are stored in environment variables.
Externalizing configuration is key to service elasticity and scalability in the cloud-native era.
For example, Kubernetes ConfigMap and Secret perfectly fit this concept.
🔧 Modern Extension:
- Use Vault/SealedSecret to manage sensitive configurations;
- Adopt Service Mesh (such as Istio) to automatically inject runtime configurations.
4️⃣ Backing Services — Treat External Services as Replaceable Resources
Principle: External dependencies (databases, message queues, caches) should be decoupled as "accessory resources" and can be freely switched.
Microservices should not hardcode service addresses or access logic but dynamically bind through configuration.
For example, local Redis and cloud Elasticache should be switched without modifying the code.
🔧 Modern Extension:
- Use Service Discovery (Consul, Eureka, Kubernetes DNS) for dynamic binding;
- Use API Gateway (Kong, Istio Gateway) for unified external access entry.
5️⃣ Build, Release, Run — Separate Build, Release, and Run
Principle: Build, Release, and Run should be three independent stages.
This separation ensures build repeatability and version traceability.
The build artifact should be immutable, for example, identified by a Docker Image.
🔧 Modern Extension:
- CI/CD Pipeline (GitHub Actions, GitLab CI, ArgoCD) for automated build;
- Immutable Artifact: Once built, the artifact cannot be modified.
6️⃣ Processes — Applications Should Be Stateless Processes
Principle: The application does not save state at runtime, and state should be managed by external services (databases, caches, object storage).
This is key to cloud-native scalability.
Any scalable system must allow service nodes to be stateless to enable horizontal scaling (Scale-Out).
🔧 Modern Practice:
- Session Externalization (Redis/Memcached);
- Distributed Storage (S3/MinIO, Etcd, PostgreSQL Cluster).
7️⃣ Port Binding — Expose Services Through Ports
Principle: Services should run independently and expose APIs through ports.
In Microservices, each service is an independent process and does not depend on external containers (such as Tomcat) to start.
For example, a Go or Node.js Microservice directly listens on a port to provide HTTP interfaces.
🔧 Modern Extension:
- Kubernetes Service + Ingress;
- API Gateway manages cross-service communication and security policies.
8️⃣ Concurrency — Scale Services Through Process Models
Principle: When scaling services, use multiple process instances instead of multithreading within a single process.
This is naturally compatible with containerization: each instance runs independently, and Kubernetes or a container orchestration system handles load balancing.
🔧 Modern Extension:
- Use Horizontal Pod Autoscaler (HPA) for automatic scaling;
- Use Service Mesh + Metrics (Prometheus) for dynamic scaling decisions.
9️⃣ Disposability — Fast Startup and Graceful Shutdown
Principle: Services should start quickly and shut down gracefully.
Fast startup enables elasticity and scalability, and graceful shutdown prevents request interruption or data loss.
🔧 Modern Extension:
- Kubernetes Lifecycle Hook (preStop/postStart);
- Graceful Shutdown handles SIGTERM signals;
- Readiness Probe prevents traffic from coming in too early.
🔟 Dev/Prod Parity — Keep Development, Testing, and Production Environments Consistent
Principle: The three environments should be as similar as possible to avoid "deployment errors."
🔧 Modern Practice:
- Infrastructure as Code (IaC): Terraform/Ansible;
- Use the same container images, database versions, and dependencies;
- Simulate the production environment with LocalStack and Minikube.
11️⃣ Logs — Treat Logs as Event Streams
Principle: Logs should be output as streams instead of written to local files.
This allows logs to be collected, monitored, and analyzed centrally.
🔧 Modern Extension:
- ELK/EFK Stack (Elasticsearch + Fluentd + Kibana);
- OpenTelemetry + Promtail + Loki for unified observability;
- Combine with distributed tracing (Jaeger, Tempo) for full-link monitoring.
12️⃣ Admin Processes — Run Administrative Tasks Independently
Principle: Administrative scripts (such as migration, backup) should run independently and not affect the main process.
🔧 Modern Practice:
- Kubernetes Job/CronJob;
- Argo Workflows for data migration and cleanup tasks;
- Automated backup policies (Velero, Restic).
🚀 Summary: From 12-Factor to Cloud-Native 24-Factor
12-Factor is the foundation, and modern cloud-native applications have derived more practices from it, such as:
- Observability
- Security Shift-Left
- Automation Policies and Policy-as-Code
- Zero-Trust Network and Service Mesh
These are the extensions of the "12-Factor++" era.
🧭 Conclusion
12-Factor is not an outdated engineering specification but an evolving philosophical system.
It forms the cornerstone of Microservice development, from application architecture and configuration management to deployment and operations.
When we build modern systems in Kubernetes, Serverless, and edge computing,
every 12-Factor principle is still silently supporting the order of the entire cloud-native world.